TIME TO READ: 6 MINUTES
In 2021, a former cybercriminal gave a Daily Mail interview detailing his past activities.
The interview covers an array of shocking behavior among modern-day criminals, but one thing stood out.
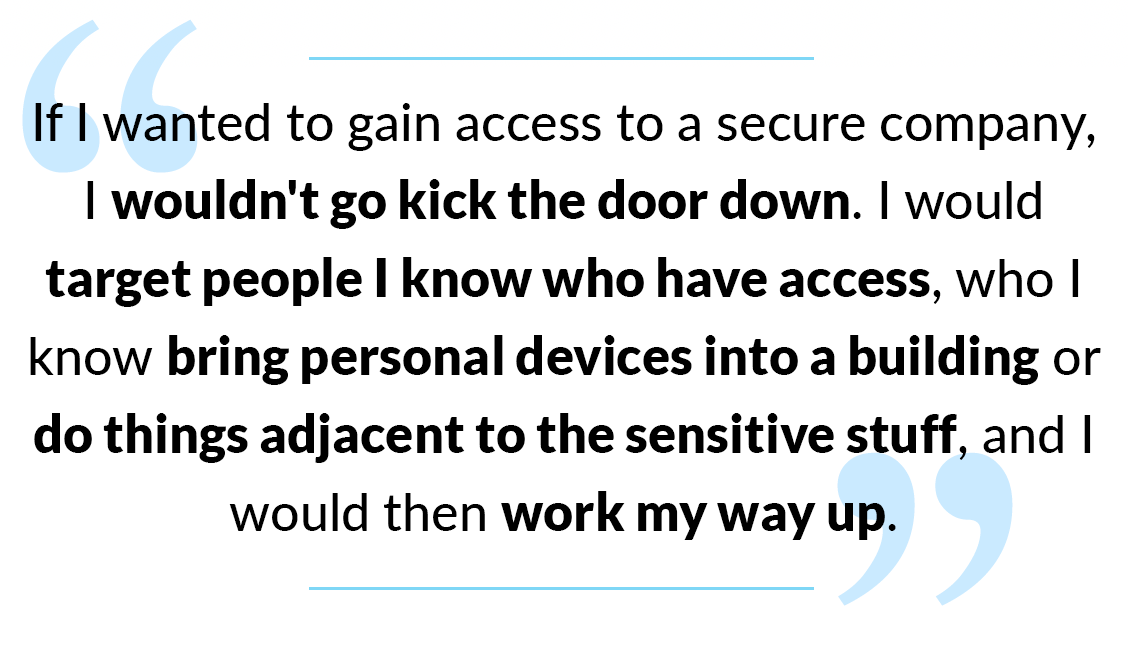
How did he break into company networks? He hijacked an employee's phone, and let the employee carry the phone inside.
Phone hijacking exploits a 'weak link' in cybersecurity...and it's gaining attention. The bad kind of attention.
Let’s go through this 'weak link' and try to strengthen it.
What a Phone Hijack Does
Basically, a phone hijack turns your phone into a Trojan Horse.
It becomes a way for cybercriminals to exploit your texts, your email, your online accounts...and your employer’s network.
How? By waiting until you bring the phone into the office where it connects to their Wi-Fi network.
(This can work on remote connections to the company network as well, if those connections have insufficient protection.)
Why? Phones store a lot of critical company data now...and they usually serve as the second factor in Two-Factor Authentication.
How a Phone Hijack Happens
The methods of phone hijacking vary immensely. You can lose control of your phone via:
- Fake apps
- Phishing emails
- Malware-infected websites
- Texts with dangerous links
- Lookalike apps (e.g., apps that look like banking apps)
The most common attack method is called “SIM Cloning” or “Simjacking.”
This uses a phishing attempt, often in the form of a malicious email, which targets the phone’s SIM card.
Every phone either has a physical SIM card or an eSIM (digital) card. Both types can fall victim to Simjacking.
Just like phishing attacks on your desktop or laptop, a Simjacking phishing email contains an infected link, which activates malware once tapped. The malware copies the phone’s SIM card...copying all the information that makes your phone, your phone.
What does it do then? It sends the cloned SIM card data to another device. One the cybercriminal controls.
Now they’ll receive a copy of every text you get, every email you receive. Including the texts sent by Multi-Factor Authentication systems to verify your identity.
They still have the malware on your phone, too. So they can use it to gain access to other networks—including the office.
Worst of all, you may have no idea all this happened!
By breaking into a phone, cybercriminals can gain control of not only the phone, but any accounts tied to it. Personal and professional.
How to Tell if Your Phone is Hijacked
Can you tell if someone’s hijacked your phone? Sometimes.
One common sign of phone hijacking is that the phone appears to “disconnect.” It powers on, but you don’t have any signal at all, or you see “Emergency Calls Only” for a long time. Even a restart doesn’t fix it.
These signs may also appear:
- You’re suddenly locked out of your Apple ID or Google Account
- You receive MFA verification requests you didn’t ask for
- New apps appear on your phone
- Battery life drops like a stone
- You see new photos/videos in your phone’s gallery...and you didn’t take them
- You lose access to online accounts, such as your bank or the company network (Source: Ryan Toohil, CTO of Aura)
Post-Hijack Actions
Once a cybercriminal has your phone under their control, they can do almost anything…and they do.
These are a few examples of what can happen to a hijacked phone:
- Cryptocurrency laundering (using your phone to steal cryptocurrency from others)
- Accessing your email
- Seizing your passwords
- Routing funds out of your bank accounts to them
- Setting up phony accounts in your name (and sticking you with the bill)
- Gaining access to your company network
The last one is the “Trojan Horse” problem we mentioned earlier. Through one compromised phone, a cybercriminal can steal millions of dollars from corporate accounts. Siphon away confidential data on thousands of customers. Inject ransomware.
All the bad stuff you hear about (and more).
It only takes one compromised phone from a high-level manager or CEO to wreak havoc.
How Companies Can Prevent Phone Hijacking and Protect Their Networks
Hijacks are insidious. Without safeguards specifically targeting phones, they can sneak past perimeter cybersecurity.
To keep them out, use these security measures.
Provide a guest/BYOD Wi-Fi network with limited access, for employee phones and personal devices.
Use a third-party authenticator app on all employee phones for MFA. Two we could recommend are Duo and Microsoft Authenticator.
- This changes the MFA method from a text – which is tied to the phone number – to an app, which isn’t tied.
- We recommend this method to all customers. It’s a stronger security measure, and blocks a lot of phone hijack methods just by existing.
Need to maintain high security over all devices? Deploy a Mobile Device Management (MDM) solution. They give you critical phone security tools like Remote Wipe, Remote Lock, and corporate profile control.
Two MDM solutions that PlanetMagpie deploys and recommends:
- N-able MDM. Features include:
- Corporate profile setup (including security policies and configuration for Exchange, VPN, and Wi-Fi)
- Quick onboarding via SMS invitation
- Remote wipe for lost devices
- Lock a mobile device, reset a passcode, locate a lost device
- Send a message to a mobile device
- Application control (ban classes of applications that pose security risks)
- Microsoft Intune. An endpoint management system that includes laptops, desktops, and phones. Larger companies often use Intune, not just for its MDM features, but also for its BYOD tools:
- How many of your team members use their personal phones for work? Intune allows you to separate personal and company data on those devices. That way a remote wipe on a lost device won’t delete your employee’s photos and videos.
- Integrate a Mobile Threat Defense (MTD) solution. MTD identifies threats on mobile devices…and blocks any malicious code from accessing company apps/data on that device!
Protect Your Phones—They're a Huge Security Risk If You Don't
The more we use our phones for important business-related tasks, the more valuable data & account access they gain. It was only a matter of time before cybercriminals realized this…and found out those phones usually have minimal protection.
Contact PlanetMagpie to secure your phones. Make sure that you keep this cyberattack vector protected.
Ready to secure those phones? Contact PlanetMagpie's Support Team to make it secure, at info@planetmagpie.com.