Secure these and cut your chances of cyberattack by 95%
TIME TO READ: 5 MINUTES
When a burglar comes to a house, what does he do? Knock on the door and politely ask you for your house keys?
Of course not. He looks for ways to break into your house quickly, without others noticing (especially you). He's looking for an easy "point of entry" – a window you left open, a door that never quite closes.
He could always break a window or kick open a door, but that's more likely to draw attention. Given the choice, thieves will always opt for an easier, quieter method of entry.
Cybercriminals behave the same way. They spend lots of time probing networks and phishing, looking for the IT equivalent of an open window, and then use the tools at their disposal to infiltrate your network.
The 7 'Weak' Entry Points in Today's IT Systems – Including Yours
Almost every aspect of a company network has a potential "point of entry" if not secured. Let’s go through each of the 7 weakest entry points that cybercriminals target, and discuss how to defend each one.
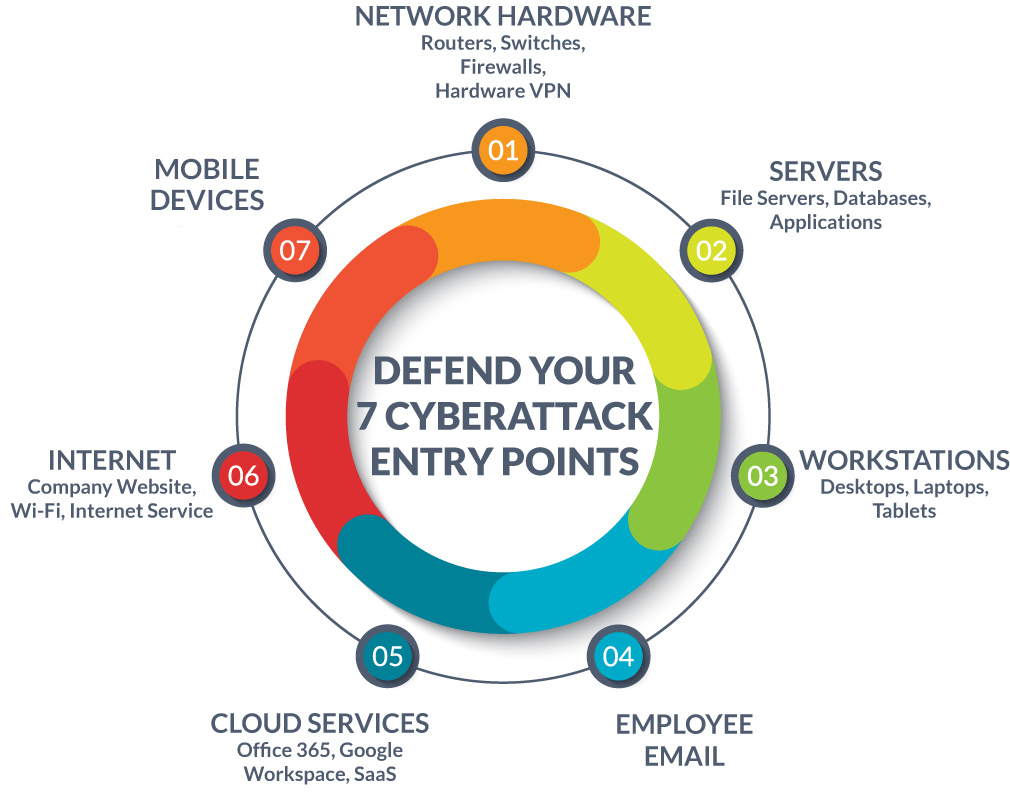

ENTRY POINT: NETWORK HARDWARE
THE RISKS:
- Unauthorized network access via your firewall, router, or Wi-Fi, using a compromised login or insecure port
- Man-in-the-middle attacks on employee communications, resulting in theft of information they thought private/secure
THE DEFENSES:

ENTRY POINT: SERVERS
THE RISKS:
- Unauthorized server access through an insecure Remote Desktop
- Loose security on file server access leads to entire servers being compromised and files being zipped up with ransomware
- Out-of-date software - operating system, hosted platforms, third-party apps
THE DEFENSES:
- "Harden" servers to limit access (a process by which entry points either close or gain protection)
- Schedule and perform regular software/firmware patching and updates
- Implement cloud backups—hosted in two different geographical locations, encrypted with versioning, tested monthly to make sure you can restore your data in an emergency
- Install an Endpoint Detection & Response solution to detect/stop malware
- Implement complex password requirements as well as password aging
- Limit both physical and network access to servers and equipment, to only those who need said access to perform their work
- Purchase cyber-insurance (your rates will be lower if you implement the recommendations in this article!)

ENTRY POINT: WORKSTATIONS
THE RISKS:
- Compromised operating systems, allowing unauthorized third-party access
- Device theft (laptop, phone, tablet, external drives)
- Malware/ransomware attacks stemming from phishing emails (see Point 3)
THE DEFENSES:
- Keep company workstations updated on the latest software/firmware
- Set workstation time-outs to 30 seconds, to avoid malicious insiders accessing another employee’s applications
- Install an Endpoint Detection & Response solution to detect and stop malware
- Implement cloud backups for your critical workstations, encrypted with versioning
- No BYOD for employees – company-approved, company-secured devices only

ENTRY POINT: EMPLOYEE EMAIL
THE RISK:
- Cyber-thieves love email. It's their favorite way to deposit malware in your network. They have a thousand ways to do it...and many of them work.
THE DEFENSES:
- Use email filtering to stop malware emails from reaching your employee inboxes in the first place
- Use business email for business (no Gmail!)
- Provide your team with cybersecurity training, so they learn to recognize phishing attacks BEFORE they click

ENTRY POINT: CLOUD SERVICES
THE RISKS:
- Targeted phishing to obtain logins to Microsoft 365, Google Workspace, Dropbox, etc.
- No backups for many cloud services (including Microsoft 365)
THE DEFENSES:
- Enable multi-factor authentication for all cloud applications whenever possible
- Pay for third-party cloud backups of your cloud applications

ENTRY POINT: INTERNET
THE RISKS:
- Remote workers using insecure Wi-Fi
- Workers visiting malware-infested websites and accidentally downloading malware
- Bot attacks on your company website forms
- Malicious insiders sending the company's Intellectual Property, financial, and customer information outside of the network for personal gain
THE DEFENSES:
- Implement a hardware VPN (virtual private network) for all remote workers
- Enforce policy of web filtering for all devices attached to the network
- Use F5 Bot Management for combatting bot attacks
- For suspected insider threats, use an insider threat detection & prevention solution to detect malicious behavior/activity

ENTRY POINT: MOBILE DEVICES
THE RISK:
- Data leaks while outside the network from hacks, malware or theft of the phone
THE DEFENSES:
- Secure with a Mobile Device Management solution that includes anti-virus and locking/remote wipe in case of loss or theft
- Don’t allow employees to use their own mobile devices for work; they should always be on a company phone that you manage
Defend Your Network Now, to Prevent Cyberattacks Later
What do thieves do with a house that's locked up tight, with alarms, surveillance cameras, and a barking dog inside? They move on to the next house.
By securing all your network entry points, you turn your company into the IT equivalent of a fortress.
Make no mistake: a Cyber War IS underway. By 2022, cyberattacks will have cost the world $6 TRILLION in damages. Scams targeting the Financial Services industry alone have gone up 423%.
Cybercriminals don’t discriminate based on the size of your company. They are opportunists and will drop their ransomware payload wherever they identify an open target.
HOPE IS NOT A STRATEGY!
DON'T BE THE NEXT CYBERATTACK VICTIM
EMAIL PLANETMAGPIE TO SCHEDULE A CYBERSECURITY REVIEW TODAY
SALES@PLANETMAGPIE.COM
What hardware and software security solutions do we trust? Check out PlanetMagpie's Cybersecurity Tech Stack here!