TIME TO READ: 4 MINUTES
How & Why Municipal Ransomware Attacks Keep Happening
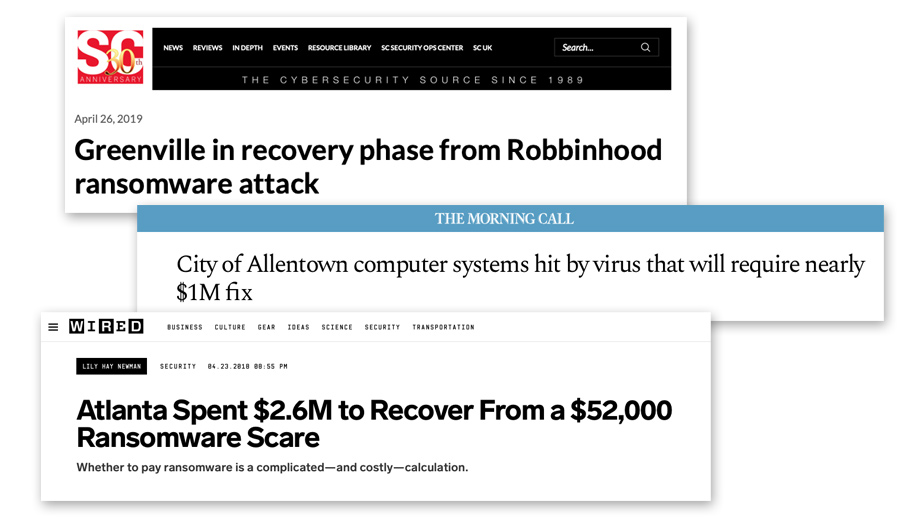
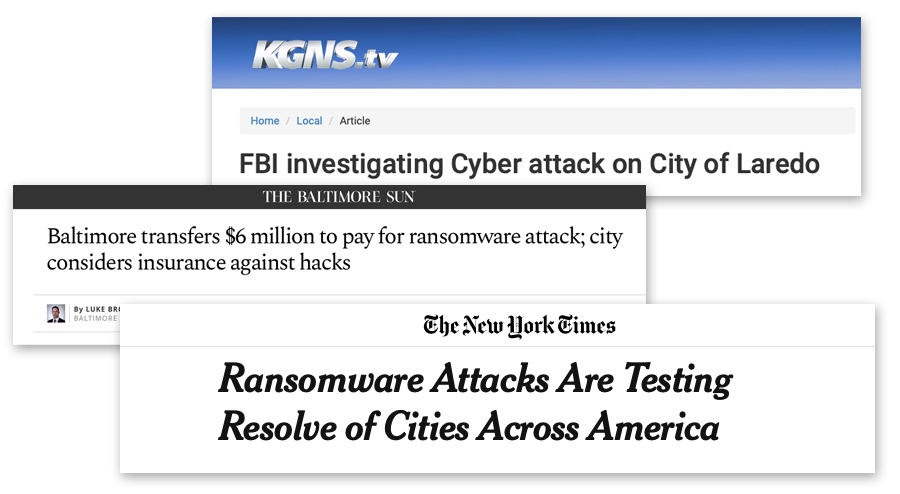
Baltimore, MD. Laredo, TX. Atlanta, GA. Allentown, PA. Greenville, NC. What do these cities all have in common?
They've suffered crushing ransomware attacks. The latest: 23 municipalities in Texas, all hit with ransomware the same weekend.
Why does this happen? Why target small towns and government offices? There is a reason...one that should give every municipality in the U.S. pause.
If you work for a municipality, or your company runs its IT on a shoestring, this WOOF is for you. We're going into the reasons why cybercriminals want to hold you hostage. Why they know it'll make them money.
And why you need to prepare...before it happens to you.
The Reasons for the Ransomware Plague on Municipalities
The harsh truth: Cybercriminals target municipalities because they're more likely to pay a ransom than a business.
The pattern started in early 2018, with attacks on cities like Atlanta. The city refused to pay, but suffered serious IT infrastructure damage.
Word got around the "bad actor" community (cybercriminals who use ransomware and other malicious tactics for profit). They hit more municipalities. Some of which paid up. This spurred more attacks. In 2019 they've refined their 'game' and show no signs of stopping.
Why do some municipalities pay up?
- They may not have consistent up-to-date backups (or no backups at all!)
- They may run older IT hardware that's more susceptible to cyberattack
- They must maintain operations 24/7, making any downtime a costly crisis (e.g., 911 operators)
- They have inadequate cybersecurity protections in place for their IT systems/website (or none at all)
The common ground on these? Imbalance between security protections & operational requirements.
In such a vulnerable position, paying the ransom seems like the "least painful" option. In reality, it's the worst—not just for your municipality, but for every city in the nation.
Why? It encourages the bad behavior. You're rewarding cybercriminals for threatening your systems. As long as you keep paying, these attacks will continue.
What about Cyber Insurance?
"Cyber insurance" is a type of insurance that covers some damages from cyber-incidents (like cyberattacks and ransomware payments).
We asked David Artzerounian of USI Insurance Services in Dallas, Texas, an experienced cyber insurance broker, his thoughts on the ransomware plague. David says that while cyber insurance can help, you need to pay close attention to the policy offered.
"One of the issues with cyber insurance in general is that there's no standardization on the offerings. Every policy needs review by an insurance broker to understand the nuances of coverage. Ransomware might not be included."
In some recent attacks on municipalities, the municipality opted to pay the ransom, and then file a claim with their cyber insurance provider to get the money back.
Now, it's cheaper to go this route if the ransom isn't too steep. But what did David think of this approach?
"I think there's a trade-off. How much is getting your data back worth to you? Do you have a way to recover the data otherwise?"
"Depending on the insurance policy you have, [this approach] may work well. Providers who've managed cyber-incidents for years have a good sense of which cybercriminals will unlock your data, and which ones will just take your money."
"You'll want to check with your cyber insurer before you pay any kind of ransom. They can help you best manage the claim. In some cases, the policy will actually pay the ransom for you."
"The bigger issue with a ransomware scenario may not be the cost of paying the ransom. It’s the downtime until you’re back up and running."
The problem: Using cyber insurance to pay the ransom doesn't guarantee you'll get your data back. In fact, less than a third of all organizations that pay get their data back.
Relying on cyber insurance to save your data won't work. What happens when cybercriminals figure this approach out, and up their ransoms accordingly?
5 Things Municipalities Can Do to Avoid Ransomware Attacks
These latest attacks on the "Texas 23" serve as a giant alarm bell. Every municipality, large and small, IS a cyberattack target.
Prepare accordingly. Here's 5 ways to do so.
- Number 1, start up an offsite cloud backup. This right here can save you. It's not expensive, nor difficult to set up. Make sure it has versioning.
- Number 2, speak with an IT expert. Either your in-house IT manager, or a security-first IT consultant like us. Listen to their advice on "hardening" your network.
- Number 3, review your IT hardware. Do you have users with older computers (4+ years old)? Does your office use older servers or software that's been running for nobody-knows-how-long? Schedule replacements for these.
- Number 4, educate yourself. Everyone working for a municipality should know what ransomware is, why they're a target, and what they need to do if hit.See the next tip for help!
- Number 5, sign up your employees for cybersecurity awareness training. It doesn't even take half a day. If even one employee deletes one phishing email instead of clicking on its link, you've saved the municipality thousands.
Municipalities – Secure Your IT! The "Ransomware Plague" is Still Happening
Businesses have woken up to the reality of cyberattacks. They're putting in backups, hardening their networks, and educating their employees.
This makes the municipality with ten-year-old hardware and zero backups the cybercriminal’s new prey. Like other criminals, cybercriminals will go after the easiest payday. If that's a City's internal network...that's where they'll strike.
PlanetMagpie wants to see every business and every municipality safe & free from worry. You provide valuable services…don't risk them with unsecured IT infrastructure. Don't become the next city on the list of ransomware victims.
Need to find out how secure your systems are? Email us at sales@planetmagpie.com for help!