Microsoft 365’s customer base continues to grow. Unfortunately, so do the cyberattacks targeting its users...like the "Puppet" scam.
Like most phishing scams, this involves sending emails laid out like M365 notices, requesting that a user provide their email and password for some reason. A link may even take you a fake "M365 portal" with a login prompt.
Once you've entered your username & password, cybercriminals capture it. Then they log in to your actual M365 account and create an email "forwarding rule." These rules tell Microsoft 365 where to send your emails.
Cybercriminals can use any of these forwarding rules:
- SPLIT FORWARDING: Creates a copy of every email & sends the copies to a different email address. You still receive all your emails. Everything looks normal. You have no idea that a copy of every single one is going to an unknown email account.
- IMPERSONATOR: Uses split forwarding, plus a rule to delete all incoming email before it reaches YOUR account. Then they impersonate you by replying to their copy of the emails.
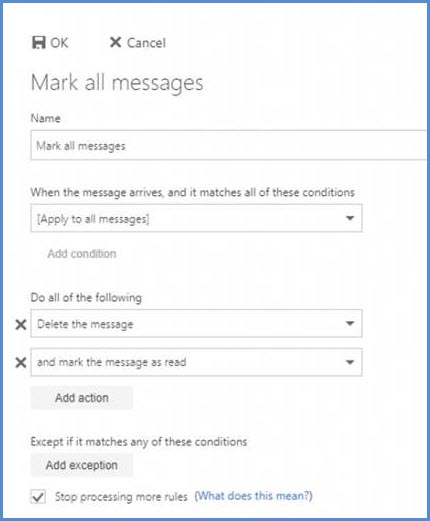
- POISON PILL: Uses your email account to post a malware-infected document on your company's OneDrive. Then they share the link with your contacts. It's in your company OneDrive, from your email address...must be legitimate, right?

Imagine how much data flows through your email every day. Now under the control of someone else. These rules act like puppet strings - hence, the "Puppet" title.
When someone creates forwarding rules in Microsoft 365, the “Tenant Admin” (often an office manager or company partner) receives an email. However, the Tenant Admin receives many auto-generated emails from M365 just from everyday administration.
They may not notice a new forwarding rule for days.
How do you combat this "puppet" phishing scam?
- First, notify your company’s Microsoft 365 Tenant Admin of this scam, so they can review email accounts for forwarding rules.
- Whenever you receive a suspicious email from M365, even if it looks official, click Reply and look at the email address. Do you see a different email than the domain-based email you'd expect from the sender? If so, delete it.
- If you have an IT support company, make sure they are set to receive the same Microsoft 365 alerts as your Tenant Admin. That way you have another set of eyes watching out.
- Implement Multi-Factor Authentication (2-step verification) like Okta on email accounts. One small change that has a big security impact.
- Deploy an email security service like modusCloud. These have "URL Defense," which identifies and auto-blocks malicious links, no matter where they originate.
Above all, remember the Universal Cyber Fu Rule: When in doubt, DON'T click the link!
Concerned about someone hacking your company's Microsoft 365 account? Please email us at sales@planetmagpie.com for help securing it.